Applied Cryptography
Table of Contents
1. Introduction
Inferno is an distributed operating system that can run on bare metal, but also as an application. We are going to use it as the basis of your applied cryptography research projects.
To grok Inferno, you need to know that it was based on the key ideas initially developped on Plan 9, namely:
- Every resource is a file (e.g. the network, the screen, the mouse).
- Each process gets its own view of the filesystem (this is called a namespace).
- One can import and export any part of the filesystem, using a protocol called 9P, locally or remotely.
The goal of these projects is to first understand then leverage how Inferno uses cryptography to secure this patchworing of resources over a potentially hostile network.
For you to feel comfortable using Inferno, a necessary condition for success in your projects, you will need to understand how the three principles above fit together to yield powerful results in very little code. A good way to do that is to look at a few examples.
2. Deliverables
On tcp!rdklein.fr!styx, an Inferno 9P server is waiting for you to upload a PDF
file. In order to connect to this file server, you will need to use inferno
yourself, and authenticate using the certificate I will provide you.
The PDF file's name must bear the family name of each member of the project team.
The first page of the PDF must bear the full name and email address of each member of the project team, as well as a well-chosen name and a short and to the point description of your work (i.e. an abstract).
The first part of the PDF report must explain how you uploaded the file to the Inferno 9P server, with what you understood of the cryptography that was involved in the process.
The second part of the PDF must detail a small software project that uses Inferno somehow, and involves cryptography. Hints to find project ideas are given below, but no ready-made project is handed over, as creativity is a huge part of engineering.
The PDF must make use of citations.
3. Grading
- If the PDF file is not given to me through the Inferno 9P server, your grade will be between 0/20 and 6/20, based on a purely subjective assessment of the content of the PDF file you somehow got me to read.
- If the PDF file was uploaded to the Inferno server, your grade will be between 6/20 and 20/20, according to the following criterion:
- Upload explanation
- A complete, precise, properly sourced, yet short explanation of how you uploaded the file will be graded over 4 points.
- You need to mention all the cryptographic concepts and algorithms that were used below the hood.
- You need to cite every important assertion, or to provide proof yourself if you can't find anything to cite in the documentation or elsewhere. This may mean writing code and running experiments to test your hypotheses, or digging into the code.
- False or wrong statements will cost points, making it possible for your grade to fall below 6/20.
- Project
- Your project will be graded out of a total of 10 points:
- Coolness
- An absolutely completely subjective and non negotiable grade out of 5 is given depending on how cool your project is. Cool does not mean huge or impressive. A simple tic-tac-toe app can be cool if the implementation is short, sweet, and elegant. A simple, working, well-understood, well-explained project is cooler than a buggy impressive one. Bugs are uncool.
- Exposition
- The other 5 points will come out of the way you explain your
work to me. I want a short, interesting document that will make me
understand what your creation is and how it works. At no point should I
have the feeling that your understanding was lacking. Here are more precise
guidelines:
- target audience
- me, your teacher, a cryptography and Inferno specialist,
- length
- short is better than meandering,
- typography
- LaTeX or *roff are your friends,
- Proof of understanding
- critical assertions should be sourced, I don't want to think that the LLM you used somehow stumbled upon the right answers. Which leads me to:
- Losing points
- It is possible for your grade to fall below 6/20, and
even reach 0/20, as the following will cause you to lose points:
- Making a wrong or false statement. Be very wary of LLMs. No LLM that I have tried knows anything deep about Inferno; but they will happily hallucinate a wrong answer. Use them if you want, but check each and every statement against the documentation and the actual behavior. If I read a factually wrong statement in your PDF, I will be very unhappy.
- Grammar and spelling mistakes. A few typos are bound to find their way into any written work, but a consistently bad spelling or grammar will make you lose points.
- Counterfactual sourcing: I will not check every sourced statement. But I will check at least one at random, and if the source does not actually validate your statement, you will lose many points. Again, be wary of LLMs, they can't source a statement correctly (yet).
4. Publication
On may 22-24 2025 the 11th International Workshop on Plan 9 will be held.
I intend to submit a paper called "Cool things my students did with Inferno", including the coolest projects, and, of course, offering a co-author seat to the students the work of whom are going to be included.
This could really kick-start your career in academia.
5. Project Ideas
5.1. Topology
Inferno is a distributed operating system. This means that the environment in which a piece of code executes is made up of many pieces borrowed from many different computers.
Imagining the optimal shape of the network of computers, the topology, for a given application, can help you find cool project ideas.
5.1.1. One server, many clients
Let's, for example, talk about the web.
Here is the model that the web has forced on us:
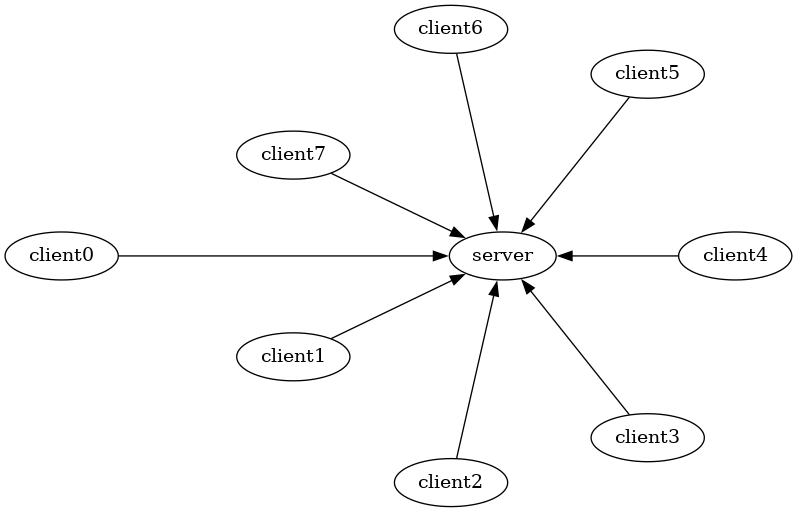
This model is not bad per-se. In fact it is the very model of the first step of this applied cryptography course: many inferno clients are going to connect to a single server to upload a PDF file each.
But inferno does it better because client authentication on the web is hard to do, whereas it comes for free in Inferno.
What is bad is that the web uses this model for everything, where other models would be more appropriate.
5.1.2. One client, many servers
For example, the following model simply reverses the web's logic:
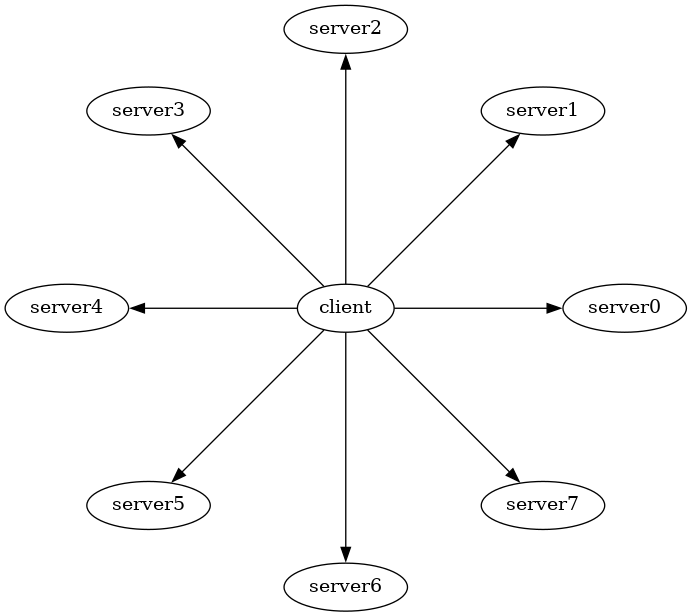
This model is very easy to implement using Inferno, and can be applied to basically any command and control or monitoring system in robotics, home automation, industrial tools, same-room multiplayer games, smart agriculture, healthcare, etc.
5.1.3. Rendez vous
At this point the limit between client and server can become blurry, especially when using Inferno, and the central host merely becomes a rendez-vous point, multiplexing the connections between many client acting as both hosts and server:
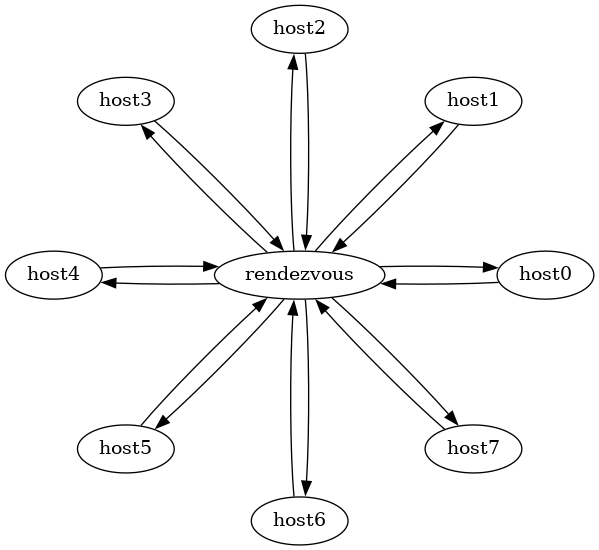 This is a useful topology for video conferencing, or any sort of collaborative app, or any online multiplayer game.
This is a useful topology for video conferencing, or any sort of collaborative app, or any online multiplayer game.
5.1.4. Distributed backend
At scale, the web today does not actually work as the naive many-clients-one-server model above, but often relies on a distributed backend for, at a minimum, load-balancing or fail-overs. This can trivially be done with Inferno:
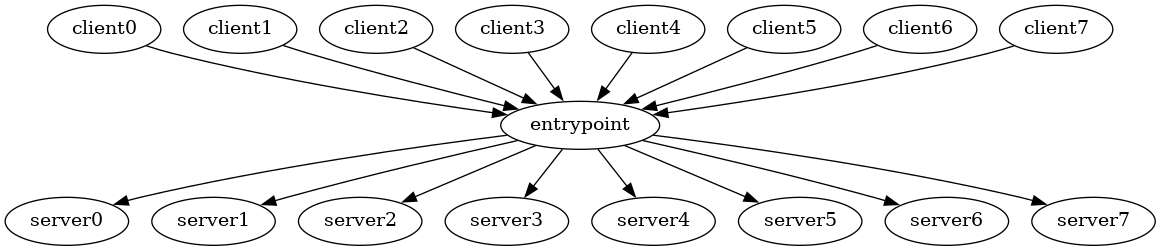
5.1.5. Peer to peer
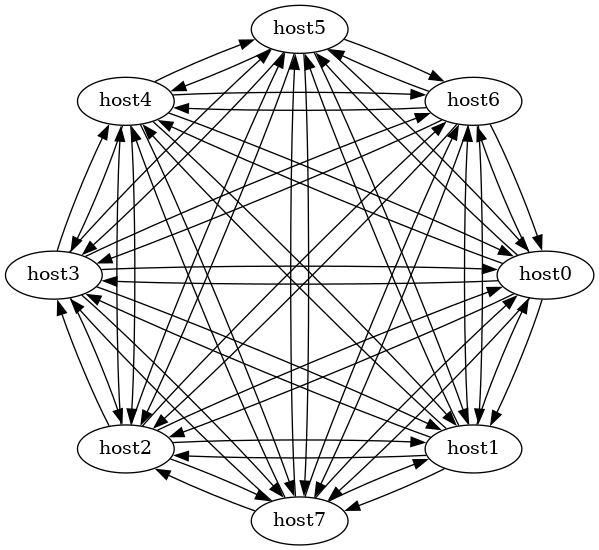 This is the topology for file sharing, blockchains, distributed version control, etc.
This is the topology for file sharing, blockchains, distributed version control, etc.
5.2. Application ideas
To help you find a fun or interesting application idea, try to list the web or mobile applications you use or know about, and try to find which topology (or mix of topologies) above would fit them better, and implement that using Inferno. You will be surprised about how little code you need.
You can also look in Inferno's source code, some demo applications are still there. You can take inspiration.
Also, you are students in a school. Many aspects of your IT system, classroom equipment, Moodle, remote learning, etc. could be better handled by Inferno. Let your frustration using those tools guide you towards imagining a better alternative.
Alternatively, watch or read some science fiction, and implement whatever gadget you see, using Inferno. I am a Star Trek: TNG fan, and I'm convinced the Enterprise is an Inferno cluster.
5.3. Inferno tools
You might want to take a look at the plumber(8), and at the registry(4).
They are helpful tool to ease communication between your Inferno instances.
5.4. Small Web
As some people gets dissatisfied with the enshitification of the web, they build alternative protocols that correct its flaws. Take for example a look at Gemini, which uses client certificates correctly. There are other small web protocols too.
5.5. Scale
Inferno can go from the Internet of Things, embedded in very low power devices, to High Performance Computing, parallelizing computation on a cluster.
Try to scale an idea down or up to make it cooler. Down is usually cooler and cheaper than up.
5.6. Helpful questions
The following questions can help you think about your work and how to write it up. Not all questions apply to all projects.
- What is the PKI ?
- What algorithms were used ?
- On which computer is the computation run ?
- On which computer is the result displayed ?
- From which computer does the input come ?
- On which computer is the data stored ? Cached ? Backed up ?
- Is there a shared secret ? Where ?
- Would this fall to a replay attack ?
- Would this fall to a man in the middle attack ?
- Would this fall to a brute-force attack ?
- Would this fall to a denial of service attack ?
- Is encryption really needed here ?
- Is authentication really needed here ?
- Is integrity checking really needed here ?
6. Avoiding Limbo
Limbo is the main programming language for Inferno. You probably won't have time to learn Limbo (but you are welcome to try, it is an interesting language that heavily influenced Go). To use any other programming language, use Inferno to build a filesystem, and re-export that filesystem locally, then mount it under Linux using the kernel's v9fs driver. You will then be able to use any programming language you like.
7. Advice
First upload a blank PDF with your names and email on it, guaranteed 6/20. Then write it up, upload again, guaranteed 10/20. Then think of something small, stupidly trivial. Make it work, write it up, upload it within the first few weeks. If done right, your grade is now guaranteed to be between 10 and 15.
Then only shoot for the moon. Base your big project on your working small project. Re-write the report often.
You will be graded on the report alone. Only if your work is cool enough will I look at the code to try to see it work.
8. Materials
9. Changelog
This page was updated for the 2024/2025 cyptography course at the ESIEA in Paris.